Help Santa Secure His Naughty List
This year I am a part of the Festive Tech Calendar and this blogpost is about securing secrets in Bicep deployments, with a festive twist.
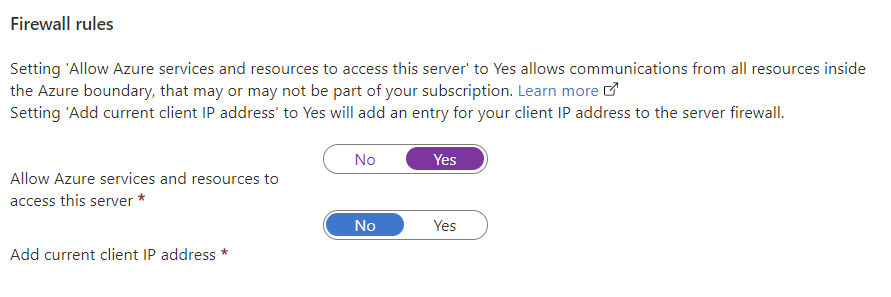
Even on the North Pole they must adopt new technologies, and Santa has started using Bicep to deploy his list of this year’s presents. Last year, Santa got a huge fine from the North pole Data Protection Authority after he committed the full naughty list into source control in a public repository. This year, Santa needs help with securing his secrets in Bicep templates during deployments!
Before I start the blogpost, I want to give a shoutout to the organizers of the Festive Tech Calendar for the amazing work they do!